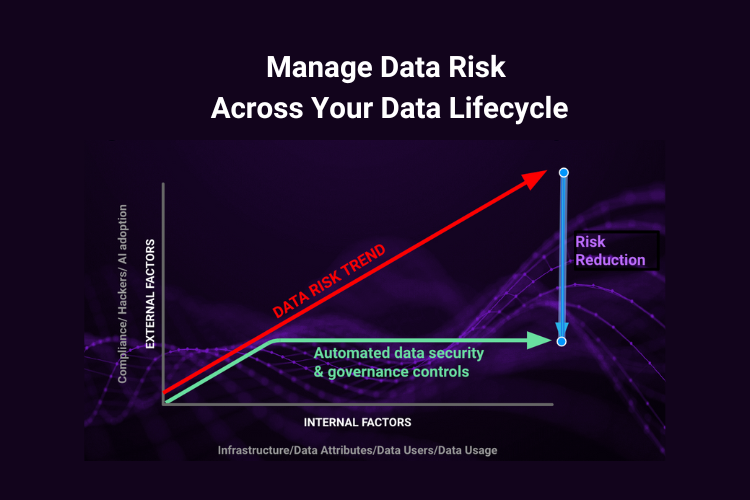
Security leaders and their teams face a stark reality: companies’ cloud and on-prem data landscapes are filled with pervasive risk and complexity, such as the threat of shadow data—unmonitored and unsecured information that evades standard security protocols. Data sprawl further complicates the scenario, with critical data dispersed across various environments, making it difficult to track, manage, and protect, and that’s just to start. These challenges are exacerbated by rapid technological advances and evolving cyber threats, placing immense pressure on organizations to maintain data integrity and security amidst an ever-expanding digital footprint.
Enter Dasera, a data security posture management (DSPM) platform designed to simplify data management from auto-discovery and classification to data-in-use monitoring across all data types and platforms. It provides a clear path to robust data governance, compliance, and security. You can walk this clear path easily and contract-free with Dasera's 'Pay as You Grow' model, which offers a scalable solution aligning with businesses' dynamic needs. This model ensures cost-effective scaling, transparent monthly billing, and the flexibility to adjust usage in response to changing security requirements, effectively addressing the operational and financial challenges of managing diverse data landscapes. With Dasera, organizations can streamline their data security processes, ensuring total data protection that evolves with their business, encapsulating a strategic approach to data security posture management.
Auto-Discovery and Low-Touch Onboarding
Auto-discovery is a cornerstone of Dasera's functionality, designed to automatically detect and catalog data stores across various platforms, such as Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. This capability goes beyond mere detection; it extends to comprehending the nature of the data, encompassing structured and unstructured data types. Structured data, typically organized in databases and tables like Redshift and Aurora MySQL, is systematically cataloged by Dasera, which identifies schemas, tables, and columns. Simultaneously, Dasera adeptly manages unstructured data in AWS S3 buckets, Microsoft 365, and Google Cloud Storage, such as documents, images, and multimedia. This nuanced approach allows Dasera to offer a comprehensive view of an organization's data landscape, highlighting its proficiency in navigating the intricacies of data storage and interrelationships across diverse environments.
This automatic discovery process is pivotal because it lays the groundwork for all subsequent data management tasks. Organizations with a clear data landscape view can better strategize their data governance, compliance, and security measures.
Once Dasera identifies the data stores and their assets through auto-discovery, the next step is onboarding these into Dasera’s system for ongoing management and analysis. The low-touch onboarding process is designed to be efficient and minimally invasive, using snapshots and APIs to integrate data environments into Dasera’s ecosystem quickly.
Snapshots provide a point-in-time picture of the data, helping to understand its current state without the need for continuous live access; however, if there are periodic snapshots taken, they can be set up for continuous monitoring as well. We just have to restore the snapshots periodically to get the incremental changes. This method is beneficial for initial assessments and setting baselines. On the other hand, APIs (Application Programming Interfaces) allow for a more dynamic interaction with the data stores. They enable Dasera to integrate with the data environments seamlessly, facilitating real-time data flow and updates between the systems. However, we should be able to achieve the same goal with either Snapshots or APIs, depending on the type of data store.
This approach to onboarding is beneficial for several reasons:
- Speed and Efficiency: Organizations can quickly connect their data environments to Dasera, reducing the time-to-value needed for their data management and analysis efforts.
- Reduced Complexity: The process minimizes the need for extensive manual setup and configuration, lowering the risk of errors and reducing the workload on IT teams.
- Scalability: As an organization’s data environment grows and evolves, Dasera’s low-touch onboarding makes adding new data stores and sources into the management framework easier.
Transitioning from the foundational processes of auto-discovery and low-touch onboarding, Dasera's next critical step involves delving into the intricacies of data management. Once the data landscapes are seamlessly integrated and mapped, the focus shifts to the sophisticated classification and configuration analysis tasks. These processes are not just about understanding what data exists and where it is stored but also about comprehensively assessing its nature, sensitivity, and the security of its environment. This progression from broad mapping to detailed examination underscores the holistic approach Dasera adopts to ensure robust data management, paving the way for enhanced data security and compliance.
Classification and Tagging
Dasera’s classification and configuration analysis capabilities are pivotal for organizations aiming to optimize their data management practices. Let’s delve deeper into how these features work and their impact on enhancing data security and compliance.
Precision in Data Identification
Dasera's classification mechanism is engineered to meticulously scan and categorize data across a broad spectrum of data stores, whether in the cloud or on-premises. This process involves identifying data types and sensitivity levels, enabling organizations to manage their data more effectively, especially when adhering to compliance regulations and securing sensitive information.
- Cloud and On-Premises Data Stores: Dasera’s classification is comprehensive, covering a range of data stores like AWS S3, Aurora PostgreSQL, Cloud SQL MySQL, and on-premises databases like Microsoft SQL Server and MySQL. This broad coverage ensures that data can be accurately classified regardless of where it is stored.
- Sensitive Data Identification: The classification process involves detecting sensitive data such as personal identification information (PII), protected health information (PHI), Payment Card Industry Data Security Standard (PCI DSS), and other data types subject to regulatory requirements. This is crucial for complying with laws and regulations like GDPR, CCPA, and HIPAA.
- Categorization and Tagging: After identification, data is categorized and tagged accordingly, which aids in implementing appropriate access controls and security measures, ensuring that sensitive data is accessed only by authorized personnel.
The Benefits of Classification and Tagging:
- Enhanced Data Governance: Tags facilitate the organization and governance of data, making it easier to locate, manage, and protect, thus improving overall data quality and usability.
- Streamlined Compliance Processes: Classification and tagging simplify, demonstrating compliance with various regulations enabling quick data retrieval for audits and regulatory inquiries.
- Improved Security Posture: By categorizing and tagging data, organizations can enforce more granular access controls, reducing the risk of unauthorized access and data breaches.
Configuration Analysis
Configuration analysis in Dasera goes beyond simple inventory checks to comprehensively examine the data store setups. This feature identifies and rectifies potential vulnerabilities or misconfigurations that could compromise data integrity and security.
- Across Platforms: Dasera conducts configuration analysis across various platforms, scrutinizing the setup of each data store, including those in AWS, GCP, Azure, and on-premises environments.
- Vulnerability Identification: By examining the configurations, Dasera identifies potential security vulnerabilities, such as inadequate access controls, unencrypted data storage, or misconfigured network settings that could expose data to unauthorized access or breaches.
- Proactive Security Measures: The insights gained from configuration analysis enable organizations to rectify any identified issues proactively. This could involve tightening access controls, enabling encryption, or adjusting network configurations to enhance security.
Impact and Benefits
The combination of classification and configuration analysis in Dasera equips organizations with the tools and insights to significantly enhance their data governance, security, and compliance postures. Here’s a closer look at the impact and benefits of these features:
- Improved Data Governance: Dasera’s classification allows organizations to clearly understand their data landscape, categorizing data based on sensitivity and relevance. This clarity is crucial for effective data governance, enabling businesses to make informed decisions about data usage, storage, and retention policies.
- Enhanced Data Security: By identifying sensitive data and potential vulnerabilities in data store configurations, Dasera helps organizations prioritize their security efforts. This targeted approach ensures that the most critical data receives the highest level of protection, reducing the risk of data breaches and unauthorized access.
- Streamlined Compliance: Compliance with data protection regulations is a significant concern for many organizations. Dasera’s classification and configuration analysis facilitate compliance by ensuring sensitive data is identified, appropriately managed, and protected according to regulatory standards. This capability helps avoid legal and financial penalties and builds trust with customers and stakeholders.
- Proactive Risk Management: The insights provided by configuration analysis enable organizations to address vulnerabilities before they are exploited proactively. This proactive approach to risk management can save substantial resources and prevent damage to the organization’s reputation.
- Operational Efficiency: Automating the classification and configuration analysis processes with Dasera reduces the need for manual interventions, saves time, and reduces the likelihood of human error. This efficiency allows IT and security teams to focus on more strategic tasks and initiatives.
Building on the meticulous classification and thorough configuration analysis, Dasera focuses on the intricate landscape of privileges and access analysis. This transition marks a move from understanding and securing the data environment to scrutinizing who interacts with this data and how. As we progress from the structural and content-oriented aspects of data management to the dynamic, user-centric view, Dasera's privileges and access analysis capabilities come to the forefront. This next phase is crucial in ensuring that the right people have the proper access, further bolstering the organization's data security and compliance frameworks.
Privileges and Access Analysis
Privileges and access analysis are crucial for maintaining the security and integrity of an organization's data. Let's delve deeper into how Dasera handles these analyses, mainly focusing on the nuances and challenges of different data store environments.
Comprehensive Privileges Analysis
Dasera’s approach to privileges and access analysis aims to map out who has access to what within an organization’s data environment, particularly focusing on database user roles and object-level access.
- Database User Roles Retrieval: Dasera retrieves the roles assigned to users within the database, cataloging each user's access level. This process is vital for identifying the distribution of access privileges and ensuring that users possess access rights that align with their roles and responsibilities. By systematically fetching these roles, Dasera highlights potential areas where access may be overly permissive, mitigating the risk of unauthorized data exposure or security breaches.
- Object-Level Access Analysis: Beyond roles, Dasera delves into object-level access, which means analyzing who can access specific tables, rows, or columns within a database. This granularity helps identify overly broad access permissions, pinpointing where data access can be restricted without impacting business operations.
The Importance of Tailored Analysis
These challenges highlight the importance of a tailored privilege and access analysis approach. Each data store type has unique characteristics and security models, necessitating a flexible and adaptable analysis strategy.
- Custom Development for Extended Capabilities: In cases where Dasera's default capabilities may not fully cover the nuances of a particular data store, custom development or enhanced access permissions might be necessary. This ensures a comprehensive analysis that aligns with each data environment's security and operational nuances.
- Balancing Security with Operational Needs: Privilege and access analysis aims to secure sensitive data while ensuring that business operations are not hindered. Dasera strikes this balance by providing detailed insights into access levels, helping organizations enforce the least privilege principle based on the visibility they get from Dasera if they see users who should not have access to sensitive data.
- Facilitating Zero Trust Architecture: The detailed visibility gained from tailored privilege and access analysis supports implementing a Zero-Trust security model. By understanding precisely who has access to what data and why, Dasera helps organizations trust no one by default and verify everything, a core principle of Zero Trust. This approach significantly enhances the security posture by minimizing the attack surface and reducing the risk of insider threats.
After mapping who has access to what within the data environment, the focus shifts to understanding how this access is utilized in real-time, this transition from examining static access permissions to dynamic data interaction is crucial, as it not only reveals potential security vulnerabilities but also offers actionable insights into operational practices, thereby ensuring a comprehensive view of data governance and security within the organization.
Data-in-Use Monitoring
Data-in-use monitoring is a critical component of Dasera's offerings, providing essential insights into how data is accessed and utilized within an organization. Let’s delve deeper into the mechanics of this process, the capabilities Dasera offers, and the challenges faced in certain data environments.
Native and Custom Query Log Analysis
Dasera employs both native and custom query log analysis to monitor data usage, which allows for a detailed understanding of how data interacts across different platforms.
- Native Query Logs: For services like AWS Redshift and Aurora MySQL, Dasera leverages native query logs to monitor data access and usage. Native logs are integral to these platforms and provide direct insight into the queries executed against the data stores, helping identify patterns of access and potential misuse.
- Custom Query Logs: In environments where native logging is either insufficient or unavailable, Dasera can implement custom logging mechanisms. For instance, in GCP’s BigQuery, while native logs provide some insight, Dasera may enhance this with custom logs to capture more detailed information about data access patterns.
Capabilities and Insights
The data-in-use monitoring capability of Dasera offers several key insights:
- Access Pattern Tracking: Understanding who accesses what data and when is crucial for detecting anomalies or unauthorized access attempts. This helps in proactively identifying potential security breaches or insider threats.
- Data Exfiltration Detection: By analyzing query logs, Dasera can help identify patterns that may indicate data exfiltration activities, such as substantial data exports or accesses at odd hours, thereby enabling timely intervention.
- Optimization and Compliance: Beyond security, monitoring data usage helps optimize the performance of data stores and ensure compliance with data governance policies, as it provides a clear picture of how data is utilized in business processes.
- Privacy Violations Monitoring: Dasera's monitoring can pinpoint instances where an individual’s personal information is targeted, preventing privacy violations and ensuring that personal data is handled in compliance with legal and regulatory standards.
- Insider Risk Detection: Dasera's ability to track access patterns and detect abnormal activities is crucial in identifying and mitigating insider threats, enhancing the organization’s ability to effectively manage and reduce insider threats.
As Dasera enhances data security with its comprehensive monitoring capabilities, it's essential to acknowledge that security and data teams often juggle between 30 to 60 tools, each tied to annual contracts that can cumulatively cost millions while not fully utilizing their capacities. This scenario highlights the need for a low barrier-to-entry option. Dasera's 'Pay as You Grow' model addresses this challenge by offering security and data teams the opportunity to leverage a robust data security tool without the hang-ups of annual contracts, ensuring they pay only for what they use. This approach streamlines budgetary allocations and aligns financial commitments directly with actual tool utilization, optimizing overall data security investments.
Pay as You Grow: Tailored Data Security for Evolving Businesses
Dasera's 'Pay as You Grow' model is expertly designed for fast-growing companies, providing a flexible and scalable pricing structure that aligns with your business's evolving needs and cloud adoption pace. Here are the key benefits and features of this model:
- Transparent Monthly Billing: Enjoy a clear, no-surprises billing cycle with no hidden fees. Charges are adjusted monthly to reflect actual usage, ensuring you only pay for what you need.
- Dynamic Usage Adjustment: Flexibility to modify your subscription monthly, aligning with your changing security needs and avoiding the constraints of annual contracts.
- Cost-Effective Scaling: Start with a single data store at $500 per month and scale your security solutions up or down based on actual data usage and business demands.
- Comprehensive Data Store Support: Dasera supports various data stores, including AWS Redshift, S3 buckets, and GCP Cloud SQL. You're billed only for the data stores actively connected to Dasera, allowing for efficient scaling as your business grows.
- Shadow Data Management: Proactively tackles the challenge of shadow data by discovering and strategizing safeguard measures for hidden data stores, reducing security liabilities, and ensuring accountability.
- Dedicated Support: Led by our Customer Support Manager, Dasera ensures you have the necessary ongoing support for onboarding and billing, adapting to business changes, and maximizing the benefits of our services.
By adopting Dasera's 'Pay as You Grow' model, you can ensure that your data security scales seamlessly with your business, providing a robust, cost-effective solution for managing and protecting your evolving data environment.
Streamlining Data Security with Dasera
Dasera stands at the forefront of data security, offering a comprehensive suite that navigates the complexities of modern data management. From auto-discovery and low-touch onboarding to nuanced classification and configuration analysis, Dasera ensures that organizations maintain a firm grip on their data landscapes. Through meticulous privileges and access analyses, coupled with sophisticated data-in-use monitoring, it provides the insights needed to safeguard against internal and external threats. Furthermore, the 'Pay as You Grow' model disrupts traditional financial approaches to data security, addressing the operational and economic realities that CISOs face. By aligning costs with actual usage and eliminating the burden of annual contracts, Dasera presents a pragmatic and scalable solution for evolving businesses. This model, underpinned by dedicated support and proactive management of shadow data, ensures that organizations can adapt their security posture in real-time, reflecting their growth and the fluid nature of digital threats. With Dasera, companies can confidently navigate the data-driven landscape, ensuring that their security evolves as dynamically as the environment in which they operate.
Ready to take control of your data security without the burden of over-commitment? Explore Dasera's 'Pay as You Grow' model today and only pay for the protection you use. With transparent monthly billing and the flexibility to adjust your subscription as your needs evolve, Dasera empowers your organization to scale securely and cost-effectively. Don’t let budget constraints dictate your security strategy. Start with Dasera and ensure your data protection aligns with your business growth.